Introduction
Linux is often preferred over Windows for server hosting in many scenarios due to several factors, including:
Cost: Linux is open-source, reducing licensing expenses.
Performance: Efficient resource usage and strong performance.
Stability: Known for consistent uptime and reliability.
Security: Robust security model with quick vulnerability fixes.
Flexibility: Highly customizable to meet specific requirements.
CLI: Powerful command-line interface for efficient management.
Containerization: Dominant platform for Docker and Kubernetes.
Community Support: Large and active community for quick issue resolution.
Web Server Compatibility: Preferred for popular web servers like Apache ,Nginx and Litespeed.
Compatibility: Supports a wide range of software, fostering interoperability.
Linux has been more prevalent in the web hosting world, particularly in server environments, due to its open-source nature, cost-effectiveness, and robust performance. Linux servers are also susceptible to security vulnerabilities and potential attacks. Thus Securing your Linux server is paramount to protect against unauthorised access, data breaches, and other potential threats. This guide provides a comprehensive set of security practices for a Linux server.
I. Initial Server Setup
1. Update and Patch
Always keep your system up to date with the latest security patches:
In Debian based Systems
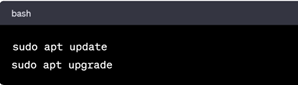
In RHEL based Systems
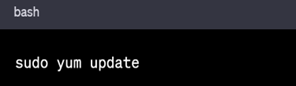
2. Create Limited User Accounts
Avoid using the root account for daily tasks. Instead, create a non-root user with sudo privileges:
In Debian based Systems
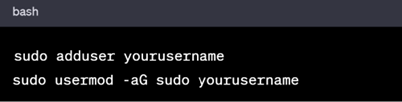
In RHEL based Systems
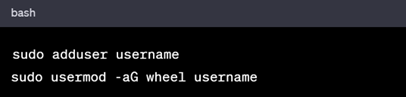
3. SSH Configuration
Enhance SSH security by:
- Changing the default SSH port.
- Disabling root login.
- Enforcing key-based authentication.
- Enable MFA for SSH login (Needs extra configurations)
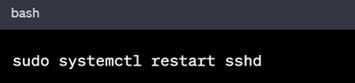
Update /etc/ssh/sshd_config and restart the SSH service:
In Debian based Systems
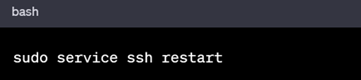
In RHEL based Systems
II. Firewall Configuration
1. Implement a firewall to control incoming and outgoing traffic:
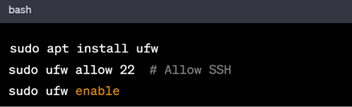
In Debian based Systems
Install UFW(Uncomplicated Firewall) and configure it
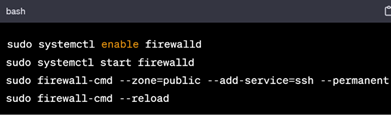
In RHEL based Systems
Install and configure Firewalld
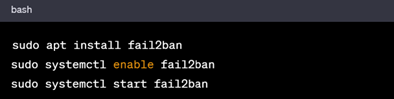
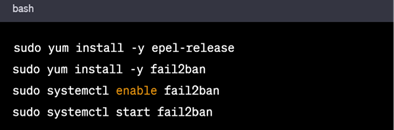
2. Fail2Ban
Install Fail2Ban to protect against brute-force attacks:
In Debian based Systems
In RHEL based Systems
III. Software Hardening
1. Disable Unnecessary Services
Identify and disable unnecessary services:
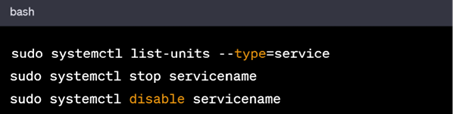
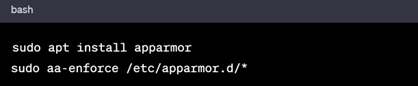
2. AppArmor or SELinux
Implement AppArmor (Ubuntu) or SELinux (Red Hat) to confine programs:
In Debian based Systems
In RHEL based Systems
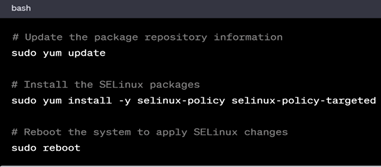
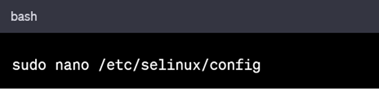
Then set SELinux to enforcing mode and reboot the system
IV. Intrusion Detection
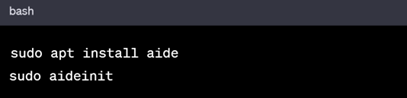
Install and configure intrusion detection tools like AIDE (Advanced Intrusion Detection Environment) or OSSEC (Open Source HIDS SECurity):
In Debian based Systems
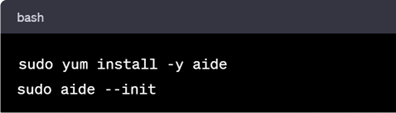
In RHEL based Systems
V. Regular Audits and Maintenance
1. Regular Audits
Conduct regular security audits to identify vulnerabilities and misconfigurations.
2. Automated Security Updates
Set up automatic security updates to ensure your system stays patched:
In Debian based Systems
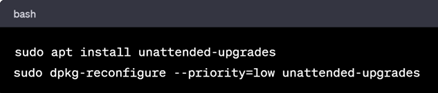
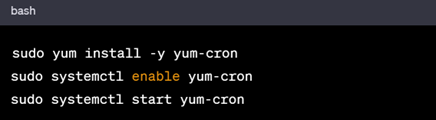
In RHEL based Systems
VI. Conclusion
Securing a Linux server is an ongoing process that requires attention to detail and continuous monitoring. By following the practices outlined in this guide, you can significantly enhance the security posture of your Linux server.
This document serves as a starting point for securing a Linux server. Tailor the recommendations to fit your specific server environment and regularly update your security practices as new threats emerge. Adjustments may be necessary based on specific requirements and use cases. Always test security configurations in a controlled environment before applying them to a production server.
Written by Maxin John.


